Vectoredge ADX
Prevent Data Exfiltration. Secure Every Endpoint.
Stay ahead of unauthorized data transfers with real-time monitoring, AI-driven intelligence, and automated security enforcement-ensuring sensitive data remains protected.
Trusted by Leading Organizations to Secure Their Data
Intelligent Data Protection
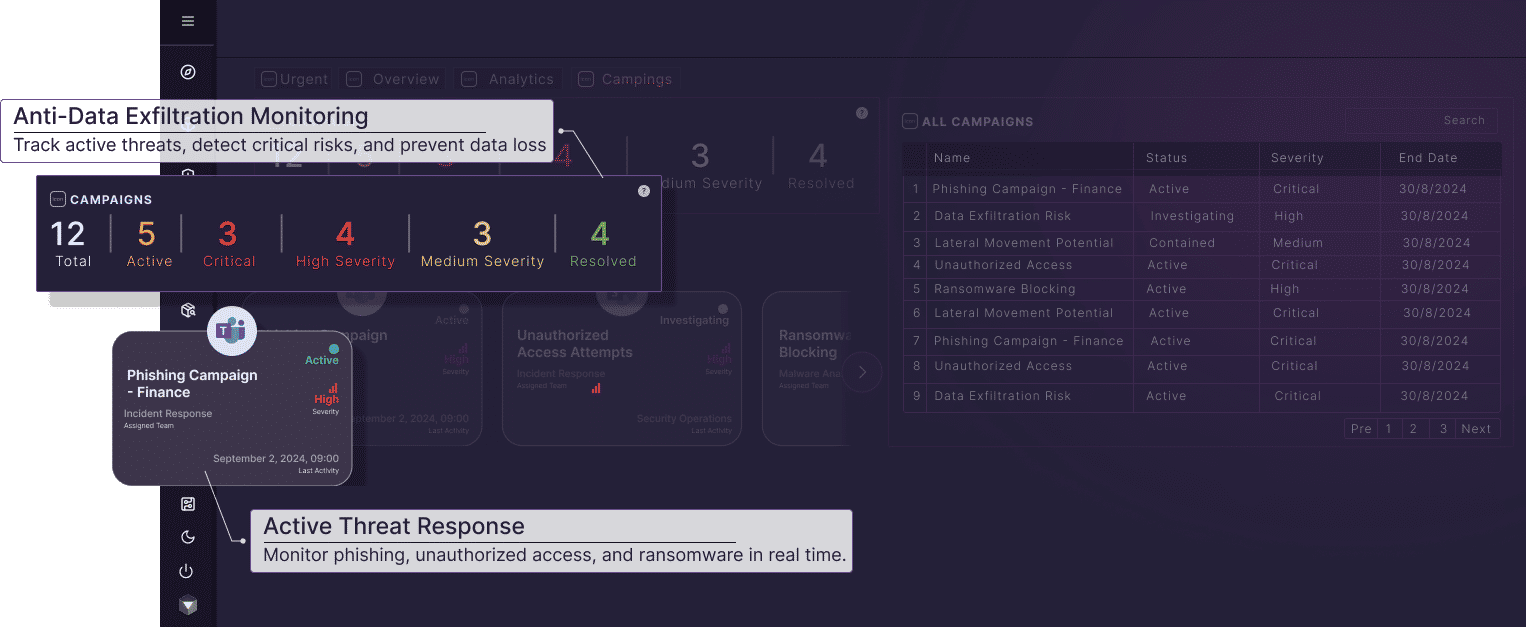
How Vectoredge ADX Protects Against Data Exfiltration
Stopping Unauthorized Data Transfers Before They Happen
The above image clearly illustrates how Vectoredge ADX actively prevents unauthorized data exfiltration across multiple channels. From cloud storage movements to file renaming and uploads to personal accounts, Vectoredge ADX ensures that sensitive information remains within corporate control. This comprehensive approach is crucial in defending against both insider threats and external attacks, ensuring real-time monitoring, intelligent policy enforcement, and immediate threat mitigation.

Cloud Data Security
Cloud environments are one of the most common points of data leakage, with employees often downloading, copying, or uploading sensitive files without realizing the potential risks. Vectoredge ADX monitors all file activities within cloud platforms like OneDrive, SharePoint, and other SaaS applications to prevent unauthorized data movement.
In the image, Olivia downloads and copies payroll-related data, which is automatically tracked and logged. Later, when Daniel attempts to export and rename the file to conceal its identity, Vectoredge ADX detects the anomaly and blocks the attempt before any data loss occurs. These actions ensure that files containing confidential information remain protected, preventing intentional or accidental breaches.
Proactive Insider Threat Management
Insider threats remain one of the biggest risks in cybersecurity, as employees, contractors, or compromised accounts may attempt to move sensitive data out of the organization. Vectoredge ADX uses behavioral analytics to detect suspicious activities like renaming files, exporting sensitive data, or uploading them to personal cloud storage.
In the scenario presented, Daniel tries multiple times to exfiltrate sensitive payroll files by renaming them and attempting to upload them to SharePoint (personal), Teams, and Dropbox. Each attempt is flagged and blocked in real-time, preventing insider-driven data leaks. By enforcing Zero-Trust Security Policies, Vectoredge ADX ensures that no unauthorized user can transfer or rename sensitive files undetected, significantly reducing the risk of corporate espionage, malicious intent, or accidental breaches.
AI-Powered Malware Detection
Malware, particularly ransomware, is one of the most dangerous cyber threats organizations face today. Attackers infiltrate corporate networks and attempt to exfiltrate, encrypt, or leak data. Vectoredge ADX integrates AI-powered threat detection to identify and stop malware-based data exfiltration tactics before they cause harm.
The image showcases how seemingly normal file movements could be an indicator of malicious activity. Daniel’s persistent attempts to rename and upload payroll files resemble the tactics used by ransomware operators to obfuscate data before exfiltration. By analyzing data flow and detecting unusual activity, Vectoredge ADX acts as a last line of defense—blocking malware-driven exfiltration attempts while keeping organizations compliant with regulatory requirements like GDPR, CCPA, and HIPAA.
Real-Time Exfiltration Prevention
One of the most critical aspects of modern cybersecurity is ensuring data never leaves an organization unauthorized. Traditional security solutions rely on reactive measures, detecting breaches only after data has been stolen. Vectoredge ADX takes a proactive approach, monitoring every file movement and immediately stopping unauthorized transfers.
The blocked attempts shown in the image demonstrate how Vectoredge ADX ensures continuous enforcement of security policies. By instantly stopping suspicious file uploads, renames, and external transfers, it eliminates blind spots in data security. Whether an employee is maliciously exfiltrating data or unknowingly violating compliance policies, Vectoredge ADX automatically applies security measures without disrupting business operations.
Stay One Step Ahead-Prevent Data Loss Before It Starts
Data exfiltration is one of the leading causes of financial losses, compliance penalties, and reputational damage for businesses worldwide. Organizations must take a preventative stance against threats, ensuring real-time visibility, automated enforcement, and AI-driven security intelligence.
With Vectoredge ADX, your business can:
- ✔ Stop unauthorized uploads instantly
- ✔ Detect and block hidden renames before exfiltration
- ✔ Monitor and prevent cloud data leaks in real-time
Data Theft Can Be Costly – Take Action Now.
The threat landscape is evolving, but with Vectoredge ADX, your data remains under your control-always.
Deploy Vectoredge ADX to secure your data and prevent leaks.
Why Vectoredge ADX is Essential for Data Security
Advanced Threat Prevention with Intelligent Monitoring
Vectoredge ADX leverages AI-driven behavioral analysis to continuously monitor and detect unusual data movements, ensuring that sensitive files remain protected at all times. By tracking user activities, such as file downloads, exports, renaming attempts, and unauthorized uploads, it prevents exfiltration before it occurs. The system automatically blocks suspicious actions, ensuring that employees or malicious insiders cannot bypass security controls. With Zero Trust enforcement, every data interaction is analyzed in real-time, providing unparalleled security across cloud applications and on-premise environments.
Seamless Compliance & Policy Enforcement
With evolving data protection regulations like GDPR, HIPAA, and CCPA, organizations must implement strict security measures to avoid compliance violations. Vectoredge ADX automates policy enforcement, ensuring that only authorized users can access, modify, or transfer sensitive files. It instantly flags and halts unauthorized attempts to rename or upload critical data to personal storage services, reducing the risk of insider threats, accidental data leaks, and regulatory penalties. Additionally, real-time alerts allow security teams to respond proactively before a potential breach escalates.
Lightweight, Non-Disruptive Security for Business Operations
Traditional security solutions can be intrusive and impact employee productivity, but Vectoredge ADX operates in the background without slowing down workflows. By securing endpoints, cloud applications, and collaboration platforms, it ensures that business operations continue seamlessly while maintaining high-level security. Its scalable architecture allows organizations to protect their data across multiple locations, cloud environments, and hybrid infrastructures, making it the ideal solution for businesses of all sizes looking to prevent data exfiltration efficiently.
Automated Policy Enforcement Enhances Compliance

Deploy According to Your Needs
Vectoredge ADX provides flexible deployment options to align with your security and compliance requirements.
Cloud-Based Deployment: Seamless SaaS integration with real-time monitoring and threat prevention.
On-Premises Deployment:Full data control with strict policy enforcement and regulatory compliance..
Vectoredge ADX vs Other Solutions
| Feature / Provider | Vectoredge ADX | Other ADX Solutions | Legacy ADX Solutions |
|---|---|---|---|
| Real-Time Data Exfiltration Prevention | ✔️ | ❌ | ❌ |
| Comprehensive Endpoint Security | ✔️ | ✔️ | ❌ |
| AI-Powered Detection & Response | ✔️ | ❌ | ❌ |
| Granular Data Control | ✔️ | ❌ | ❌ |
| Fast & Low-Latency Monitoring | ✔️ | ❌ | ❌ |
| Automated Compliance Reports | ✔️ | ❌ | Limited |
| Customer Support & Service | ⭐️⭐️⭐️⭐️⭐️ (24/7 with dedicated support) | ⭐️⭐️⭐️ (Limited support options) | ⭐️⭐️ (Basic support with long response times) |
Real-Time Data Exfiltration Prevention
Vectoredge ADX: ✔️
Other ADX Solutions: ❌
Legacy ADX Solutions: ❌
Comprehensive Endpoint Security
Vectoredge ADX: ✔️
Other ADX Solutions: ✔️
Legacy ADX Solutions: ❌
AI-Powered Detection & Response
Vectoredge ADX: ✔️
Other ADX Solutions: ❌
Legacy ADX Solutions: ❌
Granular Data Control
Vectoredge ADX: ✔️
Other ADX Solutions: ❌
Legacy ADX Solutions: ❌
Fast & Low-Latency Monitoring
Vectoredge ADX: ✔️
Other ADX Solutions: ❌
Legacy ADX Solutions: ❌
Automated Compliance Reports
Vectoredge ADX: ✔️
Other ADX Solutions: ❌
Legacy ADX Solutions: Limited
Customer Support & Service
Vectoredge ADX: ⭐️⭐️⭐️⭐️⭐️
(24/7 with dedicated support)
Other ADX Solutions: ⭐️⭐️⭐️
(Limited support options)
Legacy ADX Solutions: ⭐️⭐️
(Basic support with long response times)

