Vectoredge DLP
Protect Your Data. Ensure Compliance.
Gain unmatched visibility and control over your sensitive data with built-in compliance support for global regulations.

Innovative companies rely on Vectoredge to protect their data.
Intelligent Data Protection
Uncover, Classify & Secure Your Critical Data
Vectoredge empowers organizations with intelligent data discovery and classification, ensuring seamless protection across structured and unstructured sources. Identify and mitigate risks before they escalate with real-time insights into your data security posture.
By implementing automated data governance, companies can enforce compliance, secure sensitive information, and eliminate vulnerabilities proactively.
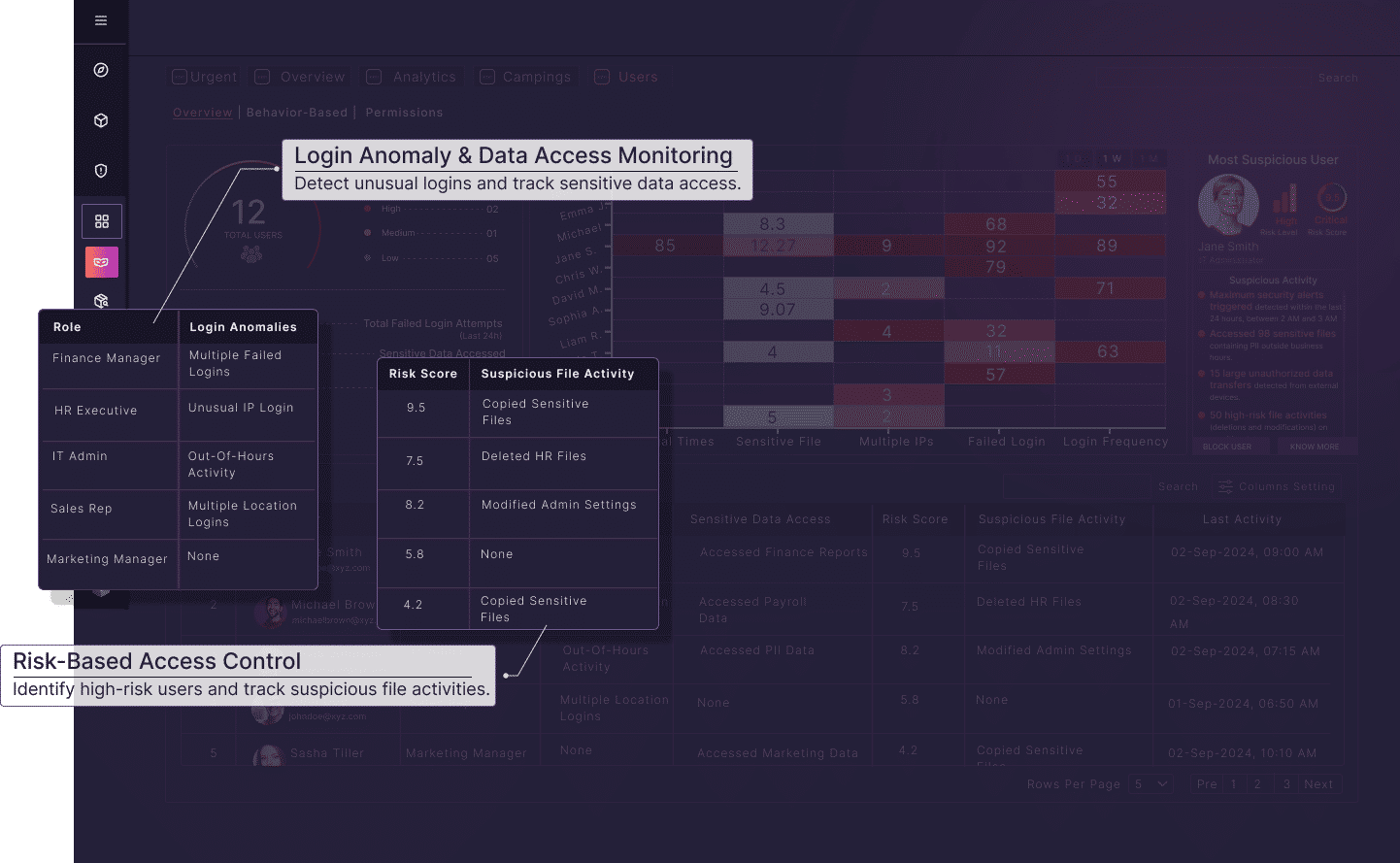
Gain Full Visibility into Sensitive Data
Data is constantly moving across cloud services, endpoints, and internal networks, making it vulnerable to leaks and breaches. Without proper oversight, businesses face regulatory and security risks.
- Automated Data Discovery, Instantly locate sensitive files, emails, and records.
- Dynamic Classification, Categorize data based on sensitivity, ownership, and policies.
- Granular Access Control, Restrict and manage access to critical data dynamically.
Continuously Monitor & Mitigate Security Risks
Misconfigurations, insider threats, and unauthorized access are key contributors to data exposure. Vectoredge ensures continuous monitoring to detect and prevent security incidents.
- Proactive Risk Detection, Identify abnormal data movements before breaches occur.
- Instant Alerts & Remediation, Receive real-time notifications on security violations.
- Automated Compliance Audits, Ensure alignment with regulations like GDPR, CCPA, and HIPAA.
Secure & Protect Regulated Data Automatically
To prevent unauthorized access and accidental data sharing, businesses need robust security measures. Vectoredge automates data tagging and enforcement policies, keeping your organization compliant.
- Intelligent Labeling, Automatically classify, tag, and secure sensitive data.
- Adaptive Encryption, Apply strong encryption controls based on data sensitivity.
- Audit Logging & Forensics, Maintain detailed logs for investigation and compliance.
Data Blind Spots? A Risk You Can't Afford.
Lack of real-time visibility into how and where sensitive data moves puts organizations at risk. Vectoredge eliminates blind spots, preventing costly security incidents.
Experience the next-gen DLP solution with Vectoredge.
Why Choose Vectoredge DLP?
Streamlined Compliance
Utilize customizable policies and over 1,700 classifiers to identify and secure Personally Identifiable Information (PII) and Protected Health Information (PHI), simplifying adherence to global data regulations.

Comprehensive Data Protection
Monitor and prevent unauthorized data transfers across cloud services, web platforms, email, and physical devices like USBs, ensuring your sensitive information remains secure.
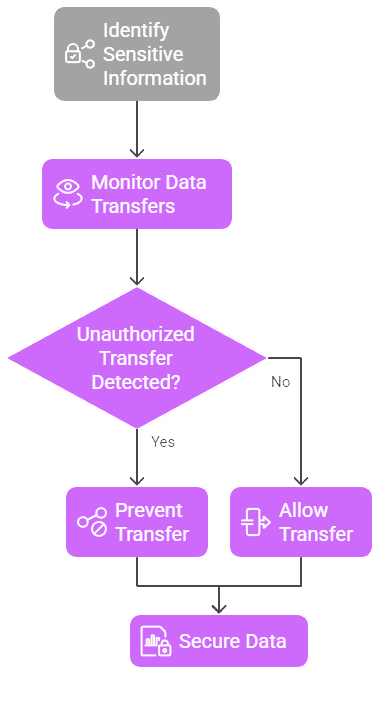
Real-Time Risk Adaptation
Analyze user behavior to predict potential risks and automatically adjust policies, proactively preventing security incidents before they occur.

Deploy According to Your Needs
Vectoredge DLP offers flexible deployment options to suit your organization's requirements:
Cloud-Based Deployment: Leverage Vectoredge's SaaS solution for seamless integration and scalability.
On-Premises Deployment: Maintain complete control over your data security with an on-premises setup.
Vectoredge DLP vs Other Solutions
| Feature / Provider | Vectoredge | Other DLP Solutions | Legacy DLP Solutions |
|---|---|---|---|
| Deployment Options | Cloud, On-Premises, Hybrid | Cloud, On-Premises | Mostly On-Premises |
| Data Movement Tracking | ✔️ | ❌ | ❌ |
| AI-Driven Risk Adaptation | ✔️ | Limited | No |
| User & Entity Behavior Analytics (UEBA) | ✔️ | Limited | No |
| Automated Policy Adjustment | ✔️ | ❌ | ❌ |
| False Positive Reduction | ✔️ AI-driven classification & tracking | Manual tuning required | Manual tuning required |
| Unified Policy Management | ✔️ | ❌ | ❌ |
| Compliance Readiness | ✔️ Yes (80+ global regulations) | Limited | No |
| Scalability | ✔️ High (Cloud-native architecture) | Medium | Low |
| Security Threat Intelligence Integration | ✔️ | Limited | No |
| Customer Support & Service | ⭐️⭐️⭐️⭐️⭐️ (24/7 with dedicated support) | ⭐️⭐️⭐️ (Limited support options) | ⭐️⭐️ (Basic support with long response times) |
Deployment Options
Vectoredge: Cloud, On-Premises, Hybrid
Other DLP Solutions: Cloud, On-Premises
Legacy DLP Solutions: Mostly On-Premises
Data Movement Tracking
Vectoredge: ✔️
Other DLP Solutions: ❌
Legacy DLP Solutions: ❌
AI-Driven Risk Adaptation
Vectoredge: ✔️
Other DLP Solutions: Limited
Legacy DLP Solutions: No
User & Entity Behavior Analytics (UEBA)
Vectoredge: ✔️
Other DLP Solutions: Limited
Legacy DLP Solutions: No
Automated Policy Adjustment
Vectoredge: ✔️
Other DLP Solutions: ❌
Legacy DLP Solutions: ❌
False Positive Reduction
Vectoredge: ✔️
AI-driven classification & tracking
Other DLP Solutions: Manual tuning required
Legacy DLP Solutions: Manual tuning required
Unified Policy Management
Vectoredge: ✔️
Other DLP Solutions: ❌
Legacy DLP Solutions: ❌
Compliance Readiness
Vectoredge: ✔️
Yes (80+ global regulations)
Other DLP Solutions: Limited
Legacy DLP Solutions: No
Scalability
Vectoredge: ✔️
High (Cloud-native architecture)
Other DLP Solutions: Medium
Legacy DLP Solutions: Low
Security Threat Intelligence Integration
Vectoredge: ✔️
Other DLP Solutions: Limited
Legacy DLP Solutions: No
Customer Support & Service
Vectoredge: ⭐️⭐️⭐️⭐️⭐️
(24/7 with dedicated support)
Other DLP Solutions: ⭐️⭐️⭐️
(Limited support options)
Legacy DLP Solutions: ⭐️⭐️
(Basic support with long response times)

