Data is the lifeblood of the digital age, powering businesses, services, and innovations worldwide. Yet, with this reliance on data comes a significant challenge: protecting sensitive data from ever-evolving cyber threats. As organizations grow, adopt cloud infrastructure, and manage increasing volumes of sensitive information, safeguarding data requires advanced strategies.
One solution rising to meet these challenges is Data Security Posture Management (DSPM). DSPM enables organizations to discover, classify, and protect data assets, providing visibility and control over potential vulnerabilities. Let’s look at DSPM, its parts, and how it can change things. We will use simple examples and real-world insights.
What is Data Security Posture Management (DSPM)?
At its core, data security posture management (DSPM) focuses on protecting sensitive data by continuously monitoring and refining security measures. DSPM offers a proactive way to reduce risks, prevent data breaches, and ensure compliance. This applies whether data is in the cloud or on-premises.
Consider this: Imagine you’re running a small e-commerce business. Your customers trust you with their credit card details, personal addresses, and preferences. What if a vulnerability in your cloud infrastructure left this data exposed? DSPM ensures this doesn’t happen by discovering and classifying sensitive data, monitoring its flows, and automating protective measures.
How DSPM Works
DSPM functions as a guardian for your data, evaluating security controls and identifying risks. Here's how it works:
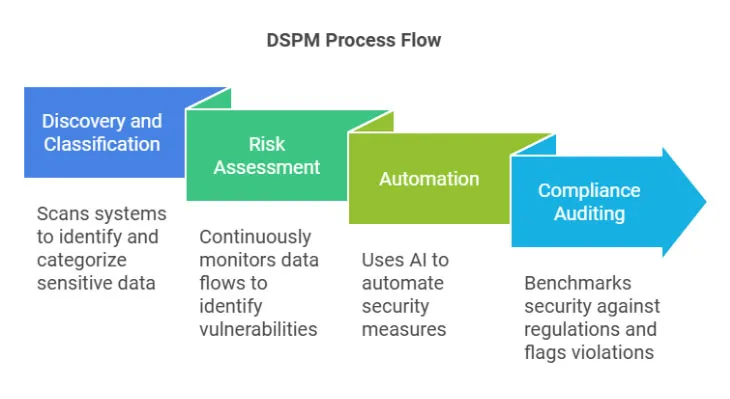
Discovery and Classification:
DSPM scans systems to discover and classify sensitive data, ensuring nothing is overlooked. This might include financial records, intellectual property, or customer details. It identifies unprotected areas of data and ensures that critical assets like personally identifiable information (PII) are categorized correctly for targeted security measures. This ensures businesses can focus their protection efforts where it matters most.
Risk Assessment
By continuously monitoring data flows, DSPM identifies and prioritizes vulnerabilities, such as excessive permissions or outdated policies. Real-time insights enable organizations to take swift action to address issues before they become exploitable. For instance, DSPM can identify shadow IT data repositories or misconfigured access points that hackers might exploit.
Automation
Using AI and machine learning, DSPM automates safeguards, making your systems adaptive and efficient. These automated processes can include enforcing data encryption, setting permission controls, and flagging unauthorized access attempts. Automation ensures businesses don’t miss critical alerts due to human error or delayed responses.
Compliance Auditing
DSPM benchmarks your security against regulations like GDPR or HIPAA, flagging violations and simplifying reporting. By doing so, it provides peace of mind to organizations operating in heavily regulated industries like healthcare, finance, and e-commerce.
Example in Action:
Imagine a healthcare provider managing patient records across a cloud-native environment. A DSPM solution detects a misconfigured access control and limits it before someone compromises sensitive information.
Key Components of DSPM
To understand its effectiveness, let’s break down DSPM into its essential components:
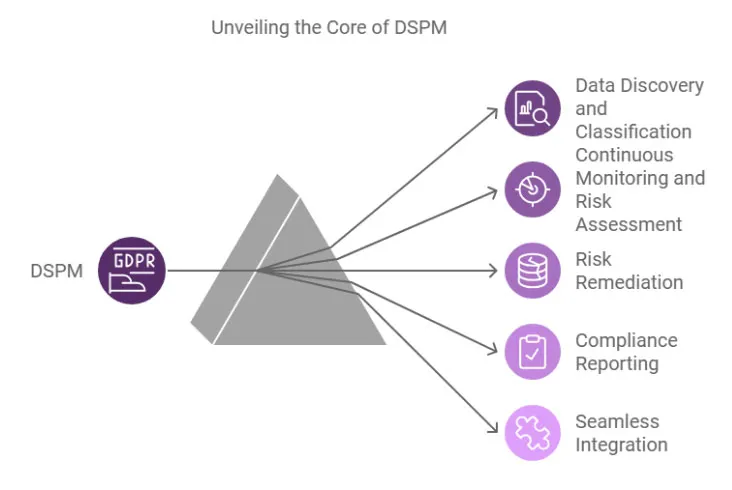
1. Data Discovery and Classification:
DSPM excels at discovering and classifying sensitive data across formats and locations. Think of it as an all-seeing eye. It finds hidden areas of important information, like unprotected data in shadow IT systems. This ability ensures businesses maintain control even as cloud environments evolve.
Effective classification includes grouping data by its sensitivity—PII, financial data, or proprietary secrets—and establishing priorities for protection. For instance, identifying intellectual property in a misconfigured storage bucket allows an organization to quickly enforce stronger access controls.
2. Continuous Monitoring and Risk Assessment:
This involves real-time continuous monitoring of your organization’s security posture. By correlating risks with real-world threats, DSPM ensures vulnerabilities don’t linger undetected. It maps how sensitive data is accessed, shared, or modified, giving organizations a comprehensive view of their data flows. This level of visibility ensures rapid identification and prioritization of risks.
3. Risk Remediation:
Once vulnerabilities are identified, DSPM offers guided remediation steps, minimizing risks at their source. For instance, if someone grants excessive permissions, DSPM highlights the issue and provides context-specific solutions. Automated tools streamline these processes, reducing the likelihood of human oversight.
4. Compliance Reporting
DSPM integrates compliance frameworks, making it easier to meet regulatory standards. By benchmarking security against industry best practices and standards, it provides actionable insights to address gaps. This ensures organizations are audit-ready, reducing stress during inspections.
5. Seamless Integration
DSPM tools work with current systems like cloud tools, SIEM systems, and IAM platforms. They strengthen defenses without interrupting operations, allowing organizations to leverage their existing infrastructure efficiently.
Why Modern Organizations Need DSPM
The need for DSPM arises from the complexities of today’s digital environments. Let’s delve into the challenges it addresses:
1. Complex Environments
Modern organizations often operate in hybrid or cloud-native ecosystems. As a result, sensitive data can become scattered across on-premises systems, SaaS applications, and cloud storage. DSPM simplifies securing data by unifying oversight across environments, ensuring no blind spots.
2. Growing Data Volumes
Statistics show global data creation is expected to exceed 180 zettabytes by 2025. Managing and protecting sensitive data across such volumes is impossible without tools like DSPM, which provide clarity and control. With the increasing adoption of AI tools, businesses also face new challenges related to data sharing and usage policies, making DSPM even more critical.
3. Evolving Cyber Threats
Every 39 seconds, a cyberattack occurs, with increasingly sophisticated techniques targeting vulnerabilities. DSPM's AI-driven capabilities detect and mitigate hidden threats effectively. By identifying patterns in real-time, businesses can prevent breaches before they occur.
4. Compliance Assurance
Regulatory violations result in hefty fines and reputational damage. DSPM aligns your data security posture with requirements, avoiding costly oversights. It also ensures that businesses remain compliant as new regulations emerge, providing long-term resilience.
5. Data Governance
When alerts flood your system without prioritization, response times lag, increasing risk. DSPM streamlines data governance by correlating alerts with risks, improving efficiency. This ensures businesses can respond quickly to the most critical threats while maintaining overall data integrity.
Benefits of Data Security Posture Management
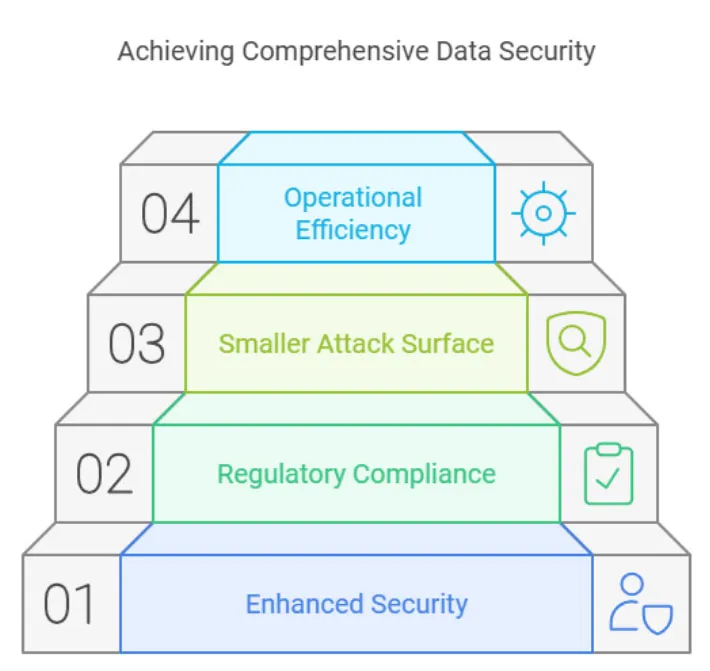
1. Enhanced Security
By automating risk identification, DSPM mitigates vulnerabilities such as misconfigurations, overly broad permissions, or unclassified sensitive information. This reduces the risk of breaches while ensuring sensitive data remains secure.
2. Regulatory Compliance
DSPM audits security measures against standards like GDPR or CCPA, ensuring both protection and peace of mind. Businesses can rely on DSPM to remain compliant, even as regulatory requirements evolve.
3. Smaller Attack Surface
DSPM offers visibility into data across cloud infrastructure, allowing precise control over policies and reducing exposure. With fewer exploitable points, attackers face greater difficulty in compromising sensitive data.
4. Operational Efficiency
DSPM’s automation relieves teams from manual monitoring, saving resources and enabling focus on strategic tasks. This ensures a streamlined approach to data security, maximizing efficiency across teams.
Why Do Businesses Trust DSPM for Data Protection? Check out our guide on DSPM Security Solutions for Data Protection .
How to Start with DSPM
Implementing DSPM requires careful planning and a solid foundation to ensure success. Here’s a detailed roadmap to get started:
1. Risk Assessment
Begin by identifying vulnerabilities and sensitive data assets within your organization. Understand where critical data resides, how it flows, and who has access. Use tools to scan for shadow IT systems or improperly managed cloud storage to uncover hidden risks. A comprehensive risk assessment sets the stage for effective DSPM deployment.
2. Define Security Controls
Based on your findings, establish protective measures tailored to your organization’s needs. For example, enforce access controls to limit permissions to only essential personnel. Define encryption standards and policies for securing sensitive data at rest and in transit.
3. Deploy DSPM
Choose a scalable, user-friendly DSPM solution that integrates seamlessly with your existing systems. Solutions like Vectoredge ensure easy adoption and powerful functionality. Look for features such as real-time monitoring, automated remediation, and detailed compliance reporting.
4. Train Your Team
Educate your IT and security teams about DSPM’s capabilities and their responsibilities. Clear communication ensures alignment on data protection goals and incident response protocols.
5. Monitor Continuously
Regularly review and adapt your data security posture. DSPM’s continuous monitoring ensures that as threats evolve, your defenses remain effective.
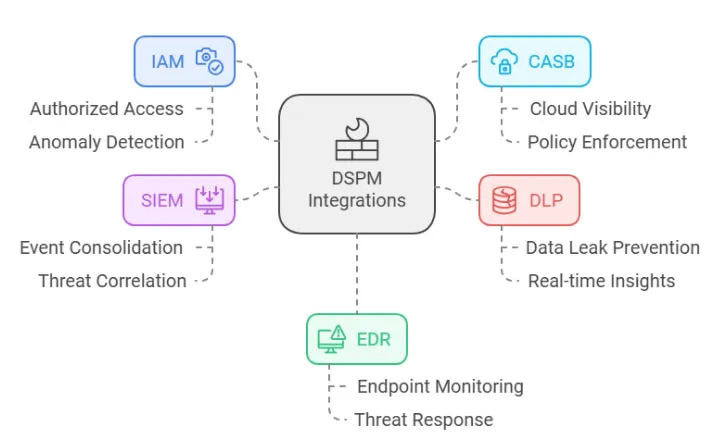
DSPM Integrations
For maximum effectiveness, DSPM integrates seamlessly with existing security tools and systems, creating a cohesive security ecosystem. These integrations ensure comprehensive protection across your data environment:
1. Identity and Access Management (IAM)
IAM tools ensure only authorized users access sensitive information. Integration with DSPM automates enforcement of access controls and monitors credential use to detect anomalies like insider threats.
2. Cloud Access Security Brokers (CASB)
CASBs provide visibility into cloud infrastructure and applications, enforcing data protection policies. Combined with DSPM, they help secure cloud-based data while extending your security posture management.
3. Data Loss Prevention (DLP)
DLP tools prevent sensitive data from leaving your environment through unauthorized channels. When integrated with DSPM, DLP policies are enhanced by real-time insights into sensitive data and its exposure.
4. Security Information and Event Management (SIEM)
SIEM systems consolidate and analyze security events for incident detection. By correlating SIEM data with DSPM insights, organizations gain broader visibility into threats and faster incident response capabilities.
5. Endpoint Detection and Response (EDR)
EDR tools monitor and respond to threats at endpoints like employee devices. Integrating DSPM with EDR ensures endpoint risks don’t compromise sensitive data, enhancing overall data asset protection.
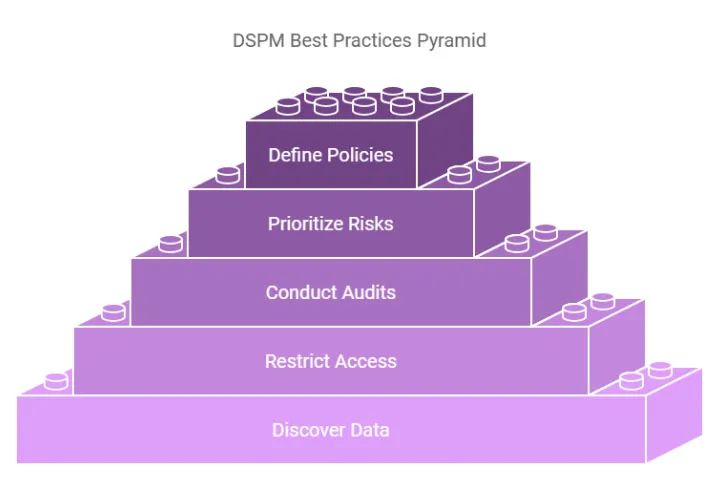
DSPM Best Practices
To maximize DSPM effectiveness, organizations should adopt the following best practices:
1. Discover and Classify Data
Achieve full visibility by identifying critical data across your ecosystem. Tag and classify structured (e.g., customer databases) and unstructured data (e.g., documents, source code). This ensures that high-value information is prioritized for protection.
2. Restrict Access
Implement least-privilege access policies, granting permissions only when necessary. Use role-based access controls (RBAC) to minimize exposure and ensure accountability for sensitive information.
3. Conduct Continuous Audits
Regularly monitor your compliance posture and adapt security controls to emerging threats. DSPM tools enable ongoing audits, ensuring alignment with regulations like HIPAA, GDPR, and PCI DSS.
4. Prioritize Risks
Focus on addressing the most critical vulnerabilities first. Use DSPM’s risk scoring to identify high-priority areas, such as overexposed data or misconfigured permissions, and act quickly to remediate them.
5. Define Clear Policies
Establish frameworks for handling and protecting sensitive data. These policies should cover data access, sharing, and disposal while aligning with industry standards. Ensuring employees are aware of and trained on these policies reduces the likelihood of errors leading to breaches.
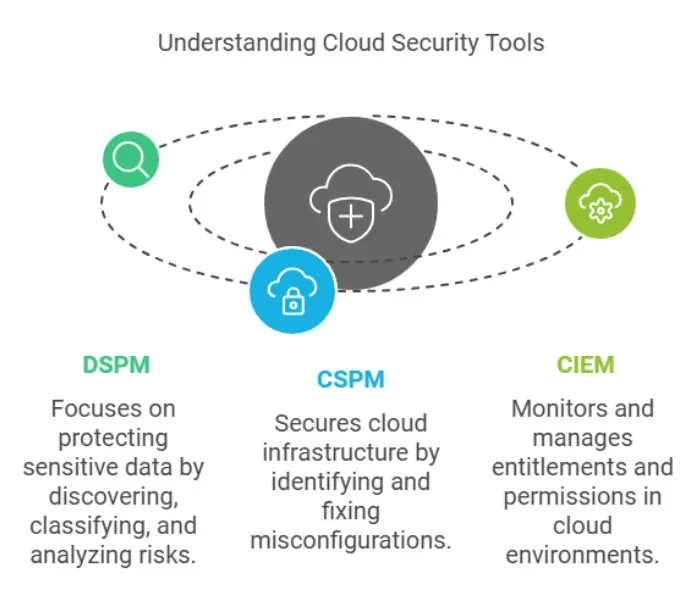
DSPM vs. CSPM vs. CIEM
To understand DSPM’s role, it’s essential to differentiate it from similar tools like Cloud Security Posture Management (CSPM) and Cloud Infrastructure Entitlement Management (CIEM). Each tool has a distinct focus within the broader security landscape:
DSPM (Data Security Posture Management)
- Focus: Protecting sensitive data by discovering, classifying, and analyzing risks.
- Example: Identifies a misconfigured database containing PII with excessive access permissions, helping prevent a breach.
CSPM (Cloud Security Posture Management)
- Focus: Securing cloud infrastructure by identifying and fixing misconfigurations.
- Example: Detects a vulnerable virtual machine running unpatched software that could be exploited by attackers.
CIEM (Cloud Infrastructure Entitlement Management)
- Focus: Monitoring and managing entitlements and permissions in cloud environments.
- Example: Flags an inactive service account with excessive permissions, reducing potential insider risks.
How They Work Together
These tools are complementary. For example, while CSPM secures the environment hosting your data, DSPM ensures the data itself is protected. CIEM further strengthens this by managing access and permissions, creating a layered defense against threats.
By combining these tools, organizations can build a robust security strategy that protects both their infrastructure and sensitive data from emerging risks.
Why Vectoredge is the DSPM Solution You Need
Vectoredge stands at the forefront of DSPM innovation. Its platform provides unified data protection across environments, leveraging AI for real-time monitoring and risk remediation.
Key Features:
- Automated data discovery and classification.
- Guided remediation for risk reduction.
- Seamless integration with existing tools like SIEM and CASB.
- Comprehensive compliance management.
With Vectoredge, organizations can confidently protect their data assets, streamline operations, and ensure regulatory alignment.
Conclusion
In a world driven by data, ensuring its security is non-negotiable. DSPM empowers organizations to safeguard sensitive information, adapt to evolving threats, and remain compliant—all while improving efficiency. Whether you’re managing an enterprise or a small business, DSPM offers the clarity and control you need to thrive.
Don’t wait for a breach to act. Explore Vectoredge’s advanced DSPM solutions today and take the first step in securing your digital future.
What’s Next?
Here are two steps you can take today to enhance your organization's data security and minimize risk:
- 1. Book a Personalized Demo Schedule a demo to see our solutions in action. We’ll customize the session to address your specific data security challenges and answer any questions you may have.
- 2. Follow Us for Expert Insights Stay ahead in the world of data security by following us on LinkedIn, YouTube, and X (Twitter). Gain quick tips and updates on DSPM, threat detection, AI security, and much more.
Foroz Farhat |
Foroz Farhat is a cybersecurity professional specializing in threat analysis, data protection, and emerging risk mitigation. With a focus on delivering actionable insights, Foroz empowers organizations to strengthen their security posture and navigate the dynamic digital threat landscape confidently.

